Unified Endpoint Management and EUC: Revolutionizing IT Management


Modern IT environments face the challenge of managing a diverse array of devices while ensuring robust security and a seamless user experience.
Unified Endpoint Management (UEM) has emerged as a pivotal solution, offering a centralized approach to oversee desktops, laptops, smartphones, tablets, and IoT devices across various operating systems.
By consolidating mobile and traditional endpoint management, UEM addresses the shortcomings of older systems like MDM and EMM, enabling IT departments to streamline operations, bolster security, and enhance employee productivity across all devices.
Understanding the core components and benefits of UEM is crucial for organizations seeking to optimize their IT infrastructure and adapt to the evolving demands of the digital workplace.

Unified Endpoint Management ( UEM ) offers a new way to manage and secure the various devices within modern companies.
With organizations facing an increasing number of endpoints, UEM solutions provide a central platform to manage desktops, laptops, smartphones, tablets, and IoT devices across different operating systems.
UEM combines the management of mobile and traditional endpoints, addressing the problems with older mobile device management (MDM) and enterprise mobility management (EMM) systems. This unified method lets IT departments simplify tasks, improve security, and increase employee output across all devices.
Important features of UEM solutions include easy device setup and provisioning, complete application management and distribution, strong security policy enforcement, and efficient operating system and software updates.
Furthermore, UEM platforms have advanced asset inventory tracking and remote monitoring and troubleshooting, giving IT teams excellent control over their endpoint environment.
Using a UEM solution has many advantages. Companies can greatly simplify their IT tasks through central management, which ensures consistent security and compliance on all endpoints.
This also improves insight into device inventory and status, streamlines software deployment and updates, and makes things better for employees through self-service features.
With more mobile and remote workers, UEM is essential for secure access to company resources from any device or place while keeping IT in control.
UEM solutions continue to develop, tackling new problems related to cloud use, IoT growth, and advanced security risks, making UEM a key part of modern IT management plans.
As organizations increasingly adopt UEM, understanding its origins and evolution becomes paramount.
For organizations seeking assistance with enterprise solutions in areas such as Datacenter and EUC Modernization, Cloudtexo offers expertise in Mobile-First Transformation, AI/IoT & Edge Computing.
The history of endpoint management solutions shows the quick technological progress and changing workplace trends of the last ten years.
This development can be seen in a few key stages, each solving the growing difficulty and variety of devices in business environments.
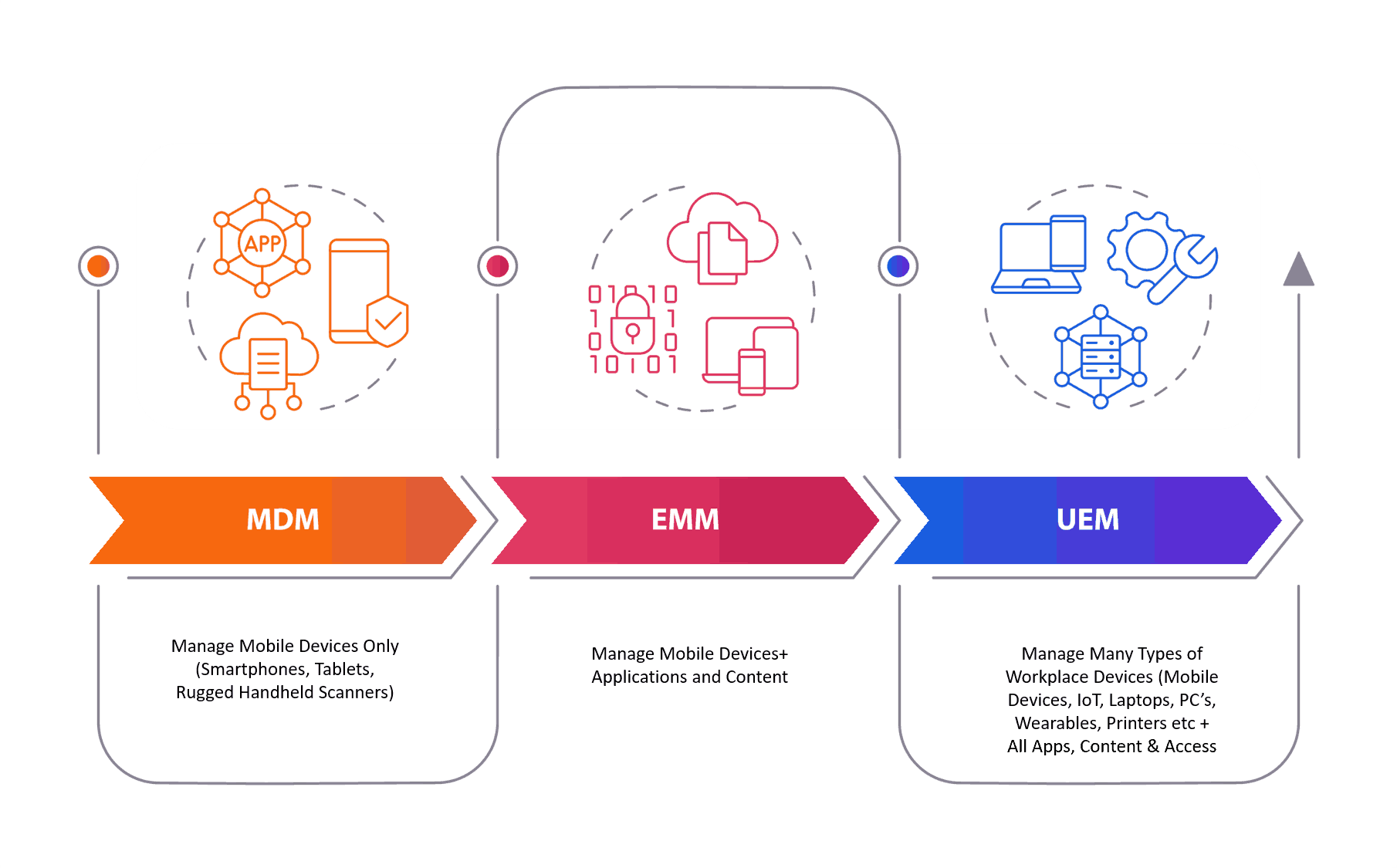
Mobile Device Management (MDM) was the first type of endpoint management, mainly for mobile devices like smartphones and tablets.
MDM solutions had basic features like device setup and configuration, remote lock and wipe functions, simple application management, and policy enforcement. Although revolutionary at the time, MDM only worked for mobile devices, leaving a gap in managing traditional endpoints.
As mobile devices became more common in business, Enterprise Mobility Management (EMM) improved on MDM features.
EMM solutions added more complex capabilities, such as mobile application management, mobile content management, and identity and access management.
This wider strategy secured and managed both company and employee-owned mobile devices that accessed company resources, reflecting the growing trend of Bring Your Own Device (BYOD) policies.
The newest development, Unified Endpoint Management (UEM), is a complete approach that combines traditional client management tools for desktops and laptops with EMM features.
This unified platform lets organizations manage and secure all types of endpoints from one place. UEM solutions work with different operating systems, including Windows, macOS, iOS, Android, and Linux, and also expand management to IoT devices.
Several factors have driven this move to UEM:
UEM solutions are still improving, adding advanced features like endpoint detection and response (EDR) and using artificial intelligence to improve security and simplify management. As the endpoint world becomes more complex, UEM is very important in helping organizations keep track, control, and secure their entire device collection.
To fully leverage UEM, it's essential to understand the key features that define its capabilities.
Unified Endpoint Management ( UEM ) software has a wide range of features designed to handle the difficult tasks of managing and securing different endpoint devices from a central platform.
These important features help organizations stay in control, improve security, and increase output across all their devices.
Device Management Across Platforms: A key part of UEM solutions is their ability to manage devices on many operating systems, including Windows, macOS, iOS, Android, and Linux. This support for different platforms makes sure that policies and management are consistent across all company devices, no matter the operating system.
Application Management and Distribution: UEM software gives IT administrators strong tools for managing the life cycle of applications. This includes the ability to remotely install and update applications, manage licenses, set up and enforce application policies, and create enterprise app stores for self-service installation. These features make sure employees can access the software they need while keeping security and compliance standards.
Security and Compliance Enforcement: UEM tools include important security features to protect sensitive data and meet legal requirements. These include device encryption management, remote lock and wipe abilities, detailed security policy enforcement, and connection with endpoint detection and response (EDR) solutions. Also, UEM platforms offer complete compliance monitoring and reporting to help organizations stay ready for audits.
Automated Patch Management: Keeping devices updated is essential for security and performance. UEM solutions simplify this by automatically finding and installing important patches, scheduling updates to reduce disruption, and providing detailed reports on patch status across all devices. This automation greatly lowers weaknesses and improves the overall security of the organization.
Remote Monitoring and Troubleshooting: UEM tools give IT teams strong capabilities for managing devices proactively. These include real-time monitoring of device health and performance, remote access for fixing problems, complete reporting on device status and issues, and automation of common support tasks. These features allow faster problem solving and better employee output.
Asset Management and Inventory: UEM software gives excellent insight into company devices by automatically finding and cataloging endpoints, tracking hardware and software inventory, managing device life cycles from start to finish, and creating detailed reports on asset use and compliance. This complete view helps organizations improve their technology investments and make sure resources are used properly.
With these strong features, UEM software helps organizations effectively manage the complexity of modern endpoint environments, improve security, and increase operational efficiency across their IT. The power of UEM is further amplified when combined with End-User Computing (EUC) strategies.
The relationship between Unified Endpoint Management ( UEM ) and End-User Computing (EUC) creates a strong system for managing and securing company devices while improving the user experience.
This mix solves important problems in modern IT and supports the changing needs of today's workers.


UEM provides central control over various endpoint devices, while EUC focuses on giving applications and data to users.
Together, they allow consistent management of both company and employee-owned devices, easy access to company resources on multiple platforms, and better security through unified policy enforcement.
This complete way to manage devices ensures that organizations can stay in control while giving flexibility to their employees.
Combining UEM and EUC greatly improves the user experience. It supports self-service features for device setup and app installation, allows personalized workspaces that follow users across devices, and simplifies access to company applications and data.
These features help improve employee output and happiness, as users can work effectively from any device or place.
From an IT point of view, combining UEM and EUC solutions offers significant benefits. It reduces difficulty through consolidated management areas, automates routine tasks like software installation and updates, and gives complete insight into device health and use.
This simplified approach allows IT teams to work more efficiently and fix potential problems before they affect users.
Security and compliance are greatly improved through the UEM and EUC combination. Organizations can enforce the same security policies on all endpoints, provide detailed control over application and data access, and allow quick response to security problems through central management.
This unified method helps maintain compliance with industry rules and internal policies, which is important in today's complex legal environment.
The UEM and EUC combination is especially valuable for supporting modern work environments, including remote and hybrid work, Bring Your Own Device (BYOD), and multi-cloud or hybrid cloud environments.
These technologies enable secure and easy access to company resources from any place or device, supporting the flexibility and mobility that today's workers need.
Successfully implementing UEM, however, requires careful consideration of best practices and potential challenges.
As organizations continue to innovate in this area, the combination of UEM and EUC will become even more important in enabling secure, efficient, and user-focused IT management plans.
By using these technologies, businesses can create a more flexible, productive, and secure digital workplace that meets the needs of both IT and users.
Putting in place Unified Endpoint Management (UEM) solutions requires careful planning to get the most benefits and handle possible problems. To make sure a UEM plan works well, organizations should think about the following best practices:
Define Clear Policies and Objectives: Start by setting up clear roles, permissions, and security rules that match company goals. Set goals that can be measured for UEM, such as improving security or allowing remote work. Clearly tell these policies to IT teams and users to make sure everyone is on the same page.
Prioritize Security and Compliance: Enforce the same security rules on all endpoints, including encryption and authentication controls. Regularly check risks and compliance to make sure you are following industry rules and internal policies. Connect UEM with current security tools and processes to create a full security system.
Ensure User Training and Adoption: Create training programs for IT staff and users to help them easily use the UEM solution. Make user-friendly guides and support to answer common questions. Think about rolling out the plan in stages to reduce disruption and allow for changes based on user feedback.
Choose the Right UEM Solution: Check potential providers based on how well they can grow, connect with other systems, and support different device types. Make sure the solution matches your company goals and IT plans. Consider things like customization and compliance features to meet specific business needs.
Regularly Update and Maintain Devices: Set up automated patch management to keep devices updated and secure. Regularly check devices and update inventory to keep an accurate view of the endpoint situation. Create a plan for managing the life cycle of all endpoints to make sure replacements and upgrades are done on time.
Despite these best practices, organizations may face several challenges when implementing UEM:
Managing Diverse Devices and Operating Systems: Making sure the same policies are used on different platforms can be hard. Keeping security standards on different devices while balancing management with user experience needs careful thought and regular changes.
Ensuring User Privacy and Data Protection: Balancing security with respect for user privacy, especially on personal devices, can be tricky. Following data protection rules while putting in place effective management controls requires a careful approach.
Integration with Existing IT Infrastructure: Connection problems with older systems may happen when putting in place UEM. Organizations must also think about how well UEM solutions can grow to meet company growth and set aside resources for connection and management.
Addressing Security Risks: Protecting against new cyber threats to endpoints is an ongoing challenge. Managing security for remote workers and putting in place zero-trust security within UEM needs constant attention and changes.
To handle these challenges, organizations should fully check their endpoint situation before starting, create a full UEM plan that matches IT and business goals, invest in training and change management, and regularly check and update UEM policies to handle new needs and threats.
As the digital landscape continues to evolve, the future of UEM and EUC in US enterprises will be shaped by several key trends.
Companies like Scalefusion offer advanced endpoint management and zero trust access solutions to help safeguard businesses with robust protection.

As US companies continue to change to fit new work environments and technological progress, Unified Endpoint Management ( UEM ) and End-User Computing (EUC) solutions will become more important in shaping the future of IT management.
There are a few key trends that will affect how these technologies are developed and used:
Integration of AI and Machine Learning: UEM platforms are adding artificial intelligence and machine learning to improve threat detection, automate routine management tasks, and provide predictions for device performance and user behavior. This helps with more proactive and efficient endpoint management, allowing IT teams to focus on important plans instead of everyday tasks.
Expansion of IoT Device Management: As Internet of Things (IoT) devices become more common in business, UEM solutions are changing to support finding and setting up different IoT endpoints, enforcing security policies for connected devices, and providing central monitoring and management of IoT assets. This helps organizations keep track of their growing IoT systems, handling the special problems that these devices cause.
Enhanced Focus on User Experience: UEM and EUC technologies are focusing more on improving the user experience through personalized device settings and app delivery, self-service features for common IT tasks, and easy access to resources on multiple devices and platforms. These improvements aim to increase employee output and satisfaction while reducing the work for IT support teams.
Adoption of Zero Trust Security Models: UEM solutions are changing to support zero trust security by using constant device authentication, providing detailed access controls based on device health and user context, and connecting with identity and access management systems. This shift helps organizations improve their security in more spread out work environments, handling the problems of securing remote workers.
As these trends continue to shape UEM and EUC, solutions are leading the way in innovation, offering advanced features that match these new needs. By using these technologies, US companies can create more secure, efficient, and user-focused IT environments that support the changing needs of modern business.
In summary, Unified Endpoint Management ( UEM ) and End-User Computing (EUC) represent a transformative approach to IT management in the United States.
As organizations grapple with the complexities of diverse device ecosystems and evolving security threats, the integration of UEM and EUC offers a pathway to streamlined operations, enhanced security, and improved user experiences.
Moving forward, businesses should prioritize strategic planning, robust security measures, and comprehensive user training to fully leverage the benefits of UEM and EUC.
By embracing these technologies, companies can create a more resilient, productive, and secure digital workplace that meets the demands of the modern business landscape.